What is an Overflow?
An overflow and underflow happen when we assign a value that is out of range of the declared data type of the variable. If the (absolute) value is too big, we call it overflow, if the value is too small, we call it underflow.
The simplest overflow is an integer overflow. This is were the arithmetic opertaion ends up with a higher value than can be stored.
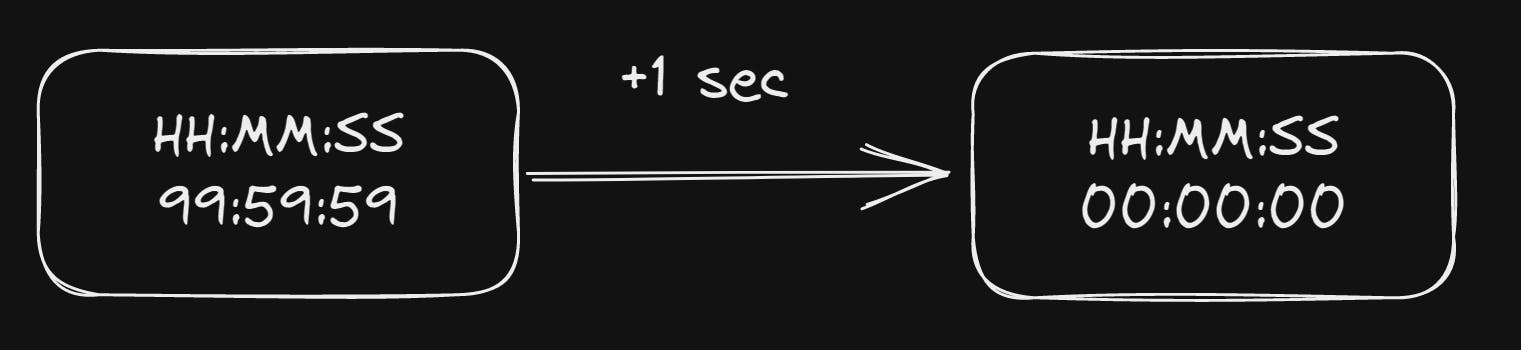
An example is a stopwatch that if you run can only store up to 100 hours is currently at 99 Hours, 59 minutes and 59 seconds and if you add one more second it overflows back to 0.
This is essentially what the Y2K bug was about. Only the last 2 digits of a year were used/stored with the assumption that it was prefixed by 19. This is happening again in the year 2038 due to the size limitation of 32-bit sign integers.
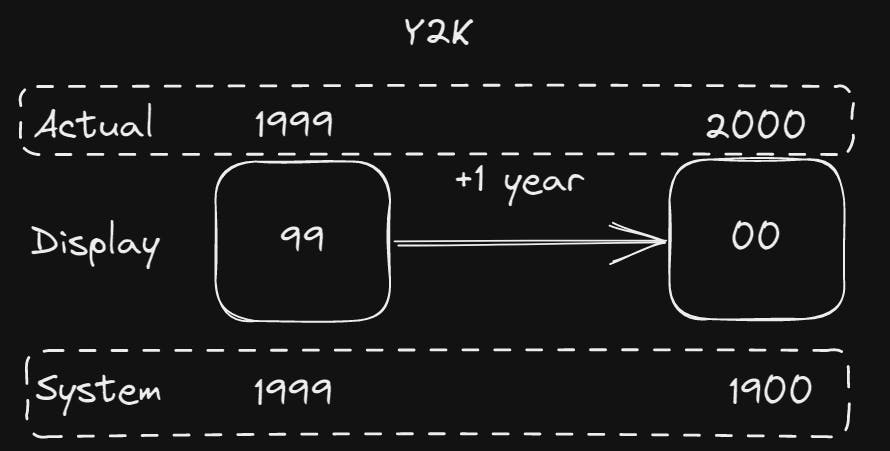
The difficulty in stopping under and overflow is that there isn't a message and the value just simply loops around unless explictedly checked.
Buffer Overflow Exploits
Buffers are temporary memory that is allocated to hold data while it is being transferred from one location to another.
When not enough memory is allocated a buffer overflow (or buffer overrun) due to the amount of data being greater than the allocated space. As a result, the data uses the adjacent memory locations and overrides the data. There are 2 types of memory stack and heap both of which can be overflowed.
Stack-based buffer overflows are more common, and leverage stack memory that only exists during the execution time of a function.
Heap-based attacks are harder to carry out and involve flooding the memory space allocated for a program beyond the memory used for current runtime operations.